Planning on buying a laptop but have no idea how to pick the right one? Take a look at our list of things you should consider before buying one!
Read more
Month: March 2016
List Of Common Mouse Problems
List Of Common Mouse Problems
Here’s a list of the most common mouse problems along with their causes and what you can do about them:
1. Mouse pointer does not move smoothly.

Main cause: Accumulation of dust at the bottom of the mouse surface.
What you can do: Clean the dust at the bottom of the mouse surface. Clean or change your mousepad.
2. Mouse pointer freezes.

Main cause: High CPU usage or hanging of some application.
What you can do: Wait a few seconds and see if the mouse starts to respond. If it doesn’t respond after a minute or so, try launching the task manager from your keyboard (Ctrl + Shift + Esc for Windows, Command + Option + Escape for Mac). If that still doesn’t work, it’s time to restart your computer.
3. Mouse doesn’t work at all.

Main cause: Loose connections or the mouse connector is connected to the wrong port.
What you can do: Check the physical connection to make sure that the mouse is properly connected to its rightful port. Still not working? Time to buy a new mouse, then.
4. Mouse pointer is too fast or too slow.

Main cause: Settings configuration.
What you can do: Open your Control Panel. Go to Mouse -> Pointing Devices -> Set mouse speed.
5. Problem with double click.

Main cause: Settings configuration.
What you can do: Open your Control Panel. Go to Mouse -> Pointing Devices -> Set mouse double click speed. Still not working? Buy a new mouse.
We hope this article helped you! Having trouble with your computer? Give us a call and we will be right at your service! Our highly experienced professional technician would love to help you fix any computer problem!
CALL US 3144 7171
or Email Us at [email protected]
How To Boost Your Computer’s Performance
How To Boost Your Computer’s Speed
1. Reduce items that run on startup.

You can customize the programs that run on startup to minimize the number of programs that take up your disk space.
Click on the Windows button -> Enter “run” -> Enter “msconfig” -> Click on “Startup” tab
2. Remove programs you no longer use.

You should regularly review which programs you no longer need and remove them. Use the Uninstaller tool from your Control Panel to uninstall programs you don’t use.
3. Clean your drive.

Type “cleanmgr.exe” into the Run menu to access Disk Cleanup. Using The Disk Cleanup frees up space by deleting useless files like temporary files created by old programs.
4. Stop using Internet Explorer if you’re still using it.

Use Google Chrome instead. It runs faster and has fewer bugs.
5. Clean your browser regularly.

Your browser also takes up a lot of your space. Go to the settings and clear your browser history, cache, and cookies regularly to free some space.
6. Regular maintenance is key.

Periodically conduct scans for viruses, spywares, and the registry errors. Regularly scan your system to get rid of any malware that may be slowing your computer down.
7. Cool your machine.

Make sure your computer has adequate air-flow around it. Use a cooling fan for your computer. Overheating will not only slow down your computer, it can also damage your hardware.
8. Note down errors.

Errors happen with systems. Note themand search for solutions online.
Feel free to consult our computer technicians if your system is having multiple complex problems. No call out fees!
CALL US 3144 7171
Skills of an Effective Computer Technician
Skills of an Effective Computer Technician
An outstanding computer technician is someone who solves all the problems with professionalism and courtesy without introducing new stresses or worries.
To be an effective computer technician, one has to acquire a certain set of skills. Here are some of the skills and traits that our computer technicians at Zoo Computer Repairs are proud to have:
A good computer technician…
Never panics.
A good computer technician understands that it’s okay to not know everything but that doesn’t mean that he won’t be able to figure it out. Part of being a technician is being excited about discovering and solving new problems. That’s how you grow. A good computer technician doesn’t fear or stress over repairs.
Is professional.
A good computer technician shows up on time and lets his clients know if he will be running late. A good computer technician dresses nicely, takes a shower, doesn’t chew gum while talking, and doesn’t use foul language. A good technician treats every service call like a job interview. If you want the client’s business now and in the future, you should be as professional as possible at all times.
Isn’t afraid to call in for backup.
A good computer technician knows that it’s okay to search the Internet if he’s unsure of what to do. Clients only really want to see their problem fixed, whatever means necessary. While clients may be impressed by a technician’s recall ability of every computer problem ever encountered, they will be infinitely more impressed when the issue is fixed correctly.
Has tools ready before arriving.
A good computer technician can squeeze by with only a few tools. However, it is always a good idea to bring all the tools required into the client’s house. A technician should really only need to go back to his car for specific hardware replacements or upgrades.
Asks plenty of questions.
A good computer technician knows that it’s always a good idea to ask questions such as “When did the problem start? Was anything changed since the problem began? What are the symptoms or error messages you’re seeing? How do you get around the problem? Would you like to know how anything else on your computer can be upgraded or improved? Do you want your computer to do anything it currently cannot do?”
Answers any questions the clients may have and lets them watch the repair process if they want to.
A good computer technician always does a good job and is proud to show it to their clients. A good computer technician is a good multitasker as well.
15 Most Dangerous Malware Of All Time
Over the years, numerous of malicious software, or malware for short, have caused all kinds of damage across computers from all over the world. Here are some of the most dangerous malware in the history of computers. To read about different kinds of malware, click here.
1. Zeus

Also known as Zbot, Zeus is a notorious Trojan which infects Windows users and tries to retrieve confidential information from the infected computers. Once installed, it tries to download configuration files and updates from the Internet. Zeus has the ability to steal information and attack banking and financial institutions around the world. Zeus is created and customized using a Trojan-building toolkit, which is available online for cybercriminals. Using the retrieved information, cybercriminals log into banking accounts and make unauthorized money transfers through a complex network of computers.
The Trojan was first identified in 2007 and has since been reduced to remnants. However, it has made a reemergence through installations of ransomware threats and spearphising campaigns associated with Dropbox. Zeus is exploited as an inexpensive and easy-to-use toolkit for hackers and remains this way today. It is known by many names including PRG and Infostealer. To date, Zeus has already infected more than 3.6 million systems in the United States. In 2009, security analysts found that Zeus has spread on more than 70,000 accounts of banks and businesses including the Bank of America and NASA.
2. Zeus Gameover (P2P) (Zeus Family)
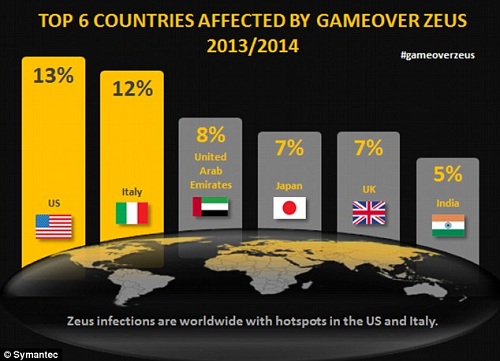
This malware is just one of the many variants of the Zeus family. This type of malware relies on a peer-to-peer botnet infrastructure. The generated peers in the botnet can act as independent Command and Control servers and are able to download commands or configuration files between them, finally sending the stolen data to the malicious servers.
Zeus Gameover is used by cybercriminals to collect financial information by targeting various user data from credentials, credit card numbers, and passwords to any other private information which might prove useful in retrieving a victim’s banking information. The malware is estimated to have infected 1 million users around the world.
Other malware from the Zeus family include SpyEye, Ice IX, Citadel, Carberp, Bugat, Shylock, and Torpig.
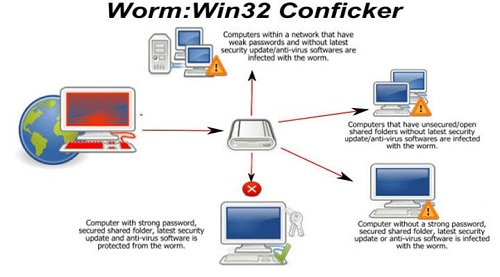
3. Conficker
The Conficker has been dubbed as a serious worm infection for Windows computers. First identified in 2008, it has been known for its aggressive attacks to disable antivirus and anti-spyware applications and then further infect systems. Specialized anti-malware tools had to be created to combat Conficker and ultimately remove it from infected computers. Many systems infected with Conficker were considered lost due to control of the computer being taken over by remote attackers.
4. CryptoLocker
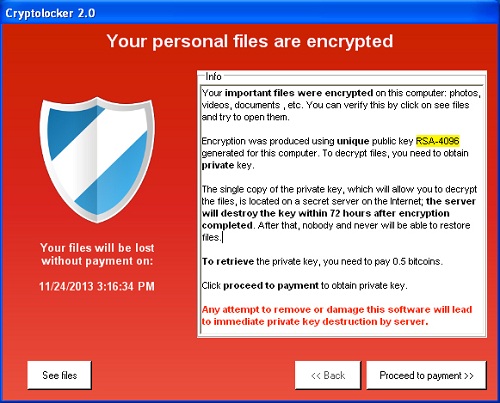
The CryptoLocker has made its name well known in the short time it has been around. The CryptoLocker is a ransomware threat that virtually locks down an infected system and does not permit usage or limited use until necessary actions are taken, such as removing CryptoLocker or entering a paid-for key code. Encryption of files was one of CryptoLocker’s major destructive actions, corrupting files and installed applications on an infected computer.
5. Qakbot
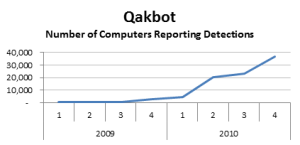
The Qakbot acts as a botnet that steals passwords and attaches itself to file shares to spread. This malware threat first emerged in 2011, making its rounds to connect to Command and Control servers waiting for instructions to carry out malicious actions on infected computers. These instruction sets provide the Qakbot the tasks of stealing login information, which then could be used by remote attackers to infiltrate online accounts such as banking accounts. A recent resurgence was noticed in September 2014 where it has so far conducted some of its well-known malicious activities.
6. Sykipot
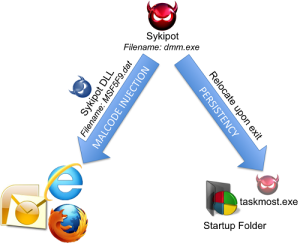
The Sykipot is a backdoor Trojan horse threat that dates back to 2007 and has had its ups and downs in its ability to bypass two-factor authentication. Such authentication measures are highly targeted in recent password-related breaches which led to massive amounts of data being stolen. The Sykipot is emerging once again and showing up in new targets, such as civil aviation and smart cards.
7. Sandworm
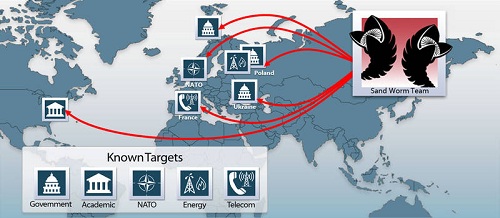
The Sandworm has been a mysterious malware threat as it has just recently made its presence well known. Although some researchers claim that it has been around as early as 2009. The Sandworm is a type of document-based malware threat that has a powerful vector for targeted attacks. The Microsoft Office has been targeted by Sandworm, highly similar to how other threats have long-attacked Adobe documents. The Sandworm uses a very effective zero-day exploit that happens to affect any version of Windows since Vista. The Sandworm is also believed to have evolved in its short lifespan to associate with socially-engineered methods to entice users to open an infected document, which will then execute its malicious code.
8. BlackPOS
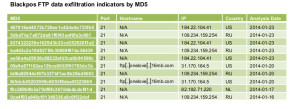
The BlackPOS is a point-of-sale malware targeting credit and debit card data swiped at POS systems running MS Windows systems. This malware was created by an individual who identifies as the “Antikiller”. The BlackPOS disguises itself as a known AV vendor software to avoid being detected in POS systems. It uses RAM scraping to grab card data from the memory of the infected POS device and exfiltrates collected data to a compromised server then uploads it to a file transfer protocol (FTP). The BlackPOS is designed to bypass Firewall software and is only 207 kilobytes in size. The crimeware kit costs $1800-$2300. Its known victims include customers of major US banks such as Chase, Capital One, Citibank, Union Bank of California, and Nordstrom Debit.
9. KOLER
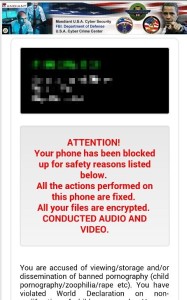
First spotted in 2014, the KOLER is an android Trojan extorting mobile device users for money to unlock their data. The Trojan poses as a valid video player that offers premium access to pornography. The KOLER automatically downloads during a browsing session. After the drive-by Trojan infects a machine, it prevents the user from accessing mobile home screens and displays a bogus message purporting to be from the national police service. The message claims the user has been accessing child abuse websites and demands payment to escape prosecution.
10. ILOVEYOU
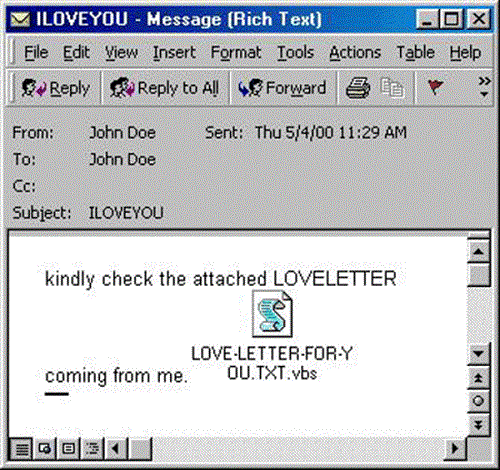
The ILOVEYOU virus is considered to be one of the most infectious computer viruses ever created. The virus managed to wreak havoc on computer systems all over the world, causing damages totaling an estimate of $10 billion. The virus was so powerful that governments and large corporations were forced to take their mailing system offline to prevent infection. The e-mail attachment disguised itself as a .txt file. However, once clicked, the ILOVEYOU virus will send itself to everyone in the mailing list and proceed to overwrite all computer files with itself, making the computer unbootable.
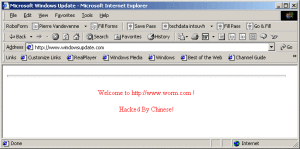
11. Code Red
The Code Red worm was first spotted in 2001 when it was discovered by two eEye Digital Security employees. The name was coined from the Code Red Mountain Dew that they were drinking at the time they discovered the worm. The worm targeted computers with Microsoft IIS web server installed, exploiting a buffer overflow problem in the system. The worm barely leaves any trace on the hard disk because it is able to run entirely on memory, with a size of just 3569 bytes. Once infected, the Code Red worm will proceed to make a hundred copies of itself but, due to a bug in its programming, will duplicate even more and end up eating a lot of the system’s resources.
The Code Red worm launches a denial of service (DoS) attack on several IP addresses (including the White House website) and allows backdoor access to the server, allowing remote access to the machine. The most memorable symptom of the said worm is a message left behind on affected web pages which says, “Hacked By Chinese!” A total of 1-2 million servers were affected and the worm caused more than $2 Billion in lost productivity.
12. Melissa
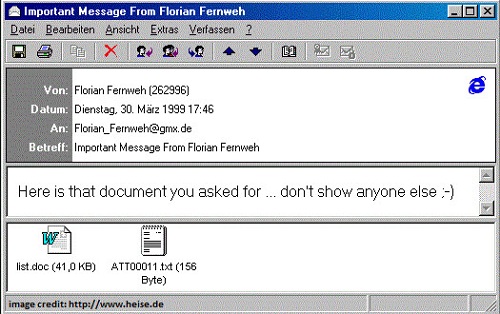
This virus was named after an exotic dancer from Florida. The virus was created by David L. Smith in 1999. The virus started as an infected Word document that was posted up on the alt.sex UseNet group, claiming to be a list of passwords for pornographic sites. The virus mails itself to the top 50 people in the user’s email address book which causes an increase of email traffic and disruption of the email services of governments and corporations. Melissa also corrupts documents by inserting a The Simpsons reference into them.
Smith served a total of 20 months in prison and paid a fine of $5000. The virus reportedly caused $80 million in damages.
13. Stuxnet
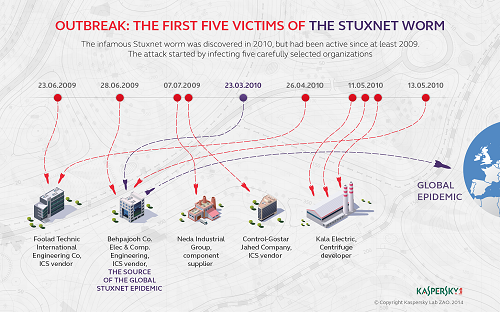
An example of a virus created for the purpose of cyberwarfare, the Stuxnet is believed to have been created by the Israeli Defense Force together with the American Government. It was created with the intention to disrupt the nuclear efforts of the Iranians. The Stuxnet managed to ruin a fifth of Iran’s nuclear centrifuges and nearly 60% of infections were concentrated in Iran. The Stuxnet was designed to attack industrial Programmable Logic Controllers (PLC), which allows for automation processes in machinery, and was specifically aimed at those created by Siemens. The virus was spread through infected USB drives. Although Siemens eventually found a way to remove the malware from their software.
14. Mydoom
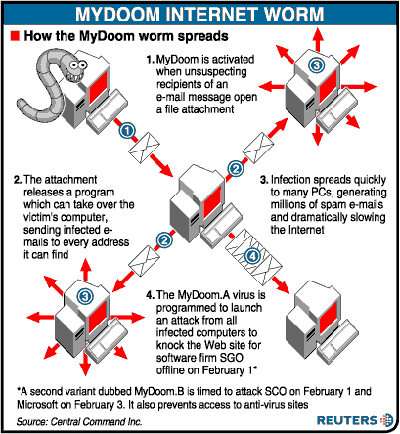
The Mydoom is a worm for Windows that became one of the fastest spreading email worms since the ILOVEYOU virus. The author remains to be unknown but is believed to have been paid to create the said worm because it contains the text message, “andy; I’m just doing my job, nothing personal, sorry,” The worm was named by McAfee employee Craig Schmugar. The name was coined from “mydom”, a line of text in the program’s code which means my domain, and the word “doom” because of the dangers the worm posed. The Mydoom spreads itself by appearing as an email transmission error and contains an attachment of itself. Once executed, the worm sends itself to email addresses that are in the user’s address book and copies itself to any P2P program’s folder to propagate itself through that network.
The payload itself is a twofold: first, it opens up a backdoor to allow remote access and second, it launches a denial of service attack on the controversial SCO Group. It is believed that the worm was created to disrupt SCO due to conflict over ownership of some Linux code. The Mydoom caused an estimate of $38.5 billion damages. The worm is still active in some form today.
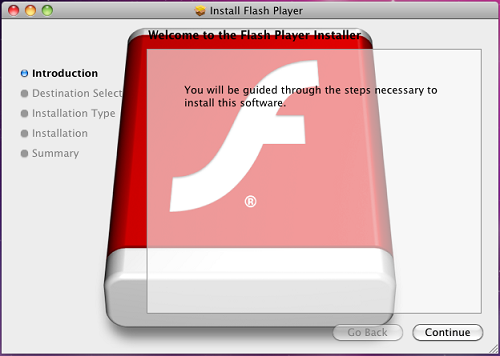
15. Flashback
The Flashback is a Trojan and is one of the few Mac malware to have gained notoriety as it showed that the Mac isn’t immune to such attacks. It was first discovered in 2011 by an antivirus company Intego as a fake Flash install. In order for the Trojan to work, the user simply needs to have Java enabled. (But who doesn’t have their Java enabled, right?) The Trojan propagates itself by using compromised websites containing JavaScript code that will download the payload. Once installed, the Mac becomes part of a botnet of other infected Macs. The good news is that, if it’s infected, it’s localized to that specific user’s account meaning the Trojan doesn’t spread anywhere else. The bad news is that more than 600,000 Macs were infected.
As of 2014, an estimate of 22,000 Macs have been infected. Oracle published a fix for the exploit with Apple releasing an update to remove Flashback from people’s Mac.
Reasons Why You Should Upgrade To Windows 10
Firewalls: Logic, Types and Rules
What is a firewall?
A firewall is a network security system, either hardware or software based that controls incoming and outgoing network traffic based on a set of rules. Firewalls act as a barrier between a trusted and other network and other untrusted networks. They filter the traffic that flows into your computer or network through an internet connection. Firewalls protect your computer by controlling access to the resources of a network through a positive control model.
Firewalls : Logic, Types and Rules
Firewall Logic
There are three types of filtering mechanisms:
Packet Filtering or Packet Purity
Data flow consists of packets of information and firewalls analyze these packets to get rid of offensive or unwanted packets depending on what you have defined as unwanted packets.
Proxy
Firewalls assume the role of a recipient and in turn sends it to the node that has requested the info and vice versa.
Inspection
Firewalls mark key features in all outgoing requests and check for the same matching characteristics in the inflow to decide if it is relevant information that is coming through.
Firewall Rules
Firewalls follow a set of rules that can be customized as per your needs, requirements, and security threat levels. You can create or disable firewall filter rules based on conditions such as:
IP addresses
You can choose to block off a certain IP address or a range of IP addresses which you think are predatory.
Domain Names
You can allow certain specific domain names to access your system/servers or allow access to only some specified types of domain names or domain extensions like .edu or .org.
Protocols
A firewall can decide which of the systems can have access to or allow common protocols like IP, SMTP, FTP, UDP, ICMP, Telnet or SNMP.
Ports
Blocking or disabling ports of servers that are connected to the Internet will help maintain the kind of data that you want to see it used for. This also closes down possible entry points for hackers or malicious software.
Keywords
Firewalls can also scrutinize through the data flow for a match of the keywords or phrases to block out offensive or unwanted data from flowing in.
Two Types of Firewall
Hardware Firewalls

Hardware firewalls can be purchased as a stand-alone product and are typically found in broadband routers. Hardware firewalls provide a strong degree of protection from most forms of attack coming from the outside world. They use packet filtering to examine header of a packet to determine its source and destination. However, hardware firewalls may be less effective that software firewalls because it’s possible for them to ignore embedded worms in outgoing e-mails and see this as a regular network traffic.
Software Firewalls

Software firewalls are the most popular firewall choice. Software firewalls are installed on your computer and can be customized. Software firewalls will protect your computer from external attempts to control or gain access to your computer. Software firewalls usually provide additional protection against the most common Trojan programs or e-mail worms. (Read about Trojans and worms *insert link here*.) They usually have user defined controls for setting up a safe file and printer sharing and to block unsafe applications from running on your system. Software firewalls may also incorporate privacy controls, web filtering and more. On the downside, software firewalls only protect the computer they are installed on, not the entire network.
Firewalls are a must for any kind of computer usage that requires going online. They protect you from all kinds of abuse and unauthorized access like Trojans that allow taking control of your computers by remote logins or backdoors, virus, or use your resources to launch DDoS attacks.
The ideal firewall configuration consists of both hardware and software. They are useful for allowing remote access to a private network through secure authentication certificates and logins.
Firewall testing is also an important part of maintenance to ensure your system is always configured for optimal protection.
Ways To Protect Your Computer From Malware
11 Ways To Protect Your Computer From Malware
We use our computer to do so many things. We google information, we go online to shop, handle our bank accounts, play games, and stay in touch with family and friends. Because of this, our computers contain a lot of information about us. This information could include banking and other financial records, as well as medical information. If your computer is unprotected, hackers, identity thieves, and other fraudsters may be able to get access and steal all your personal information. Spammers could also use your computer as a “zombie drone” to send spam that looks like it came from you. Different kinds of malware could be deposited on your computer, slowing it down or destroying your files.
It is therefore very important that you use safety measures and good practices to protect your computer so that you can also protect your privacy as well as your family.
Here are some of the things you can do to ensure your computer’s safety:
1. Install Anti-Virus/Malware Software

You’d be surprised at the number of computers, especially home computers, that don’t have anti-virus/malware protection. Installing an anti-virus onto your computer is the first step in keeping your computer protected from malware.
Free anti-virus is not the best solution but it’s better than nothing.
2. Keep Your Anti-Virus Software Up-To-Date

The first step to protecting your computer is having protection software. The second step is maintaining it. New malware gets released all the time. Keeping your anti-virus up-to-date ensures that it can protect your computer from new malware. Your scanning software is only as good as its database. Make sure that you always update it.
3. Schedule Scans To Run Regularly

Again, this is sort of a non-brainer but most of us are too busy to remember this. Setup your software of choice to run at regular intervals, most preferably once a week. It can be difficult to work on your computer while your anti-virus is running a scan so it would be a good idea to schedule it at night while you’re not using your computer. Make sure you leave the computer on and it doesn’t shut off automatically or go into hibernation mode.
4. Keep Your Operating System Up-To-Date
Operating System developers are always issuing security patches that fix and plug security leaks. These patches keep your system secure. Make sure your computer has them by keeping your operating system up-to-date. Fix your settings in such a way that you are notified when there are new updates or your computer auto-downloads the updates for you as soon as they become available.
5. Make Sure Your Network Is Secure

If you keep your Wi-Fi open, never broadcast it. Make sure that your Wi-Fi connection requires a strong password. By strong, we mean your password should be a combination of lowercase, uppercase, symbols, and numbers. Use the WPA or WPA2 encryption, not WEP. It is also never a bad idea to hide your SSID (the name of your network) so that only you can see it and malicious users won’t have access to it.
6. Think Before You Click

Be wary of what you might be getting yourself into. Avoid websites that provide pirated materials as they are more likely to contain viruses that are just waiting for your click. Do not open e-mail attachments from unknown senders. Always hover on links, especially the ones with shortened URLS, before you click on them so you can see where they are really taking you. Make sure you scan everything you download before opening them. You could also check if your antivirus software can do this automatically.
7. Protect Your Personal Information

Because of the number of social media accounts and the amount of time we spend on them, this one could actually be the hardest thing to do. However, it is important to keep your personal information private. Many hackers will access your files not by brute force, but by social engineering. Lock down all your privacy settings and avoid using your real name or identity on discussion boards.
8. Don’t Use Open Wi-Fi

Never use open Wi-Fi. Open Wi-Fi connections are Wi-Fi connections that don’t have any passwords or encryptions. If an ordinary user like you can access it so easily, what do you think an experienced hacker can do? When you setup a wireless connection at home, it is recommended to add security to it. There are several types of password that are used to secure your Wi-Fi Connection.
9. Backup Your Files

Always backup your files. You never know when you might lose them. Although data recovery is possible in some cases, it is not 100% reliable. Backup your files so you won’t have to deal with data loss. It is always safe to have your files in at least three places: where you work on them, on a separate storage device, and off-site. Keep your files on your computer, back them up to an external drive, then back them up in a different location.
10. Use Multiple Strong Passwords

Never use the same password for two or more accounts, especially your back account. Make sure that you use strong passwords (combination of lowercase, uppercase, symbols, numbers) as well. It is always a good idea to use passwords that are easy to remember but hard to guess. Don’t use dates or names.
11. Use A Firewall

A firewall is a protective system that lies between your computer network and the Internet when used correctly. Firewalls prevent unauthorized use and access to your computer. Their job is to carefully analyze data entering and exiting the network based on your configuration. Firewalls can be hardware, software, or both. Read more about firewalls here.
Differences of Virus, Worm and Trojan Horse
When something is wrong with your computer and you find out a malicious file or program is causing it, most people will automatically assume that the malicious object is a virus. However, not all malicious software are viruses. A virus is just one of the many malicious software you can encounter as a computer user. In this article we will discuss the most common types of malicious software, or malware for short. Read more
Different Types of Malware
What is Malware?
It is a common misconception that any software or file that is harmful to your computer is a virus. As a matter of fact, a virus is just one of the many types of malicious software or malware for short. Malware is the umbrella term used to refer to different kinds of hostile and intrusive software which includes computer viruses, worms, Trojan horses, ransomware, spyware, adware, and others that we will be discussing later in this article. Malware can take the form of executable code, scripts, active content, and other software.
Different Types of Malware
The most common types of malware are viruses, worms, and Trojan horses. These three are usually thought to be the same. These three are all malicious programs that can cause damage to your computer. However, learning the difference between the three, as well as all the other types of malware, can help you protect your computer better.
1. Virus

A computer virus is a man-made piece of code that has the capability to copy itself. Microsoft defines a virus as a small software program that is designed to spread from one computer to another and to interfere with computer operation. It is usually loaded onto your computer without your knowledge and will run against your will. Computer viruses typically have a detrimental effect, such as corrupting your system or destroying your data. They will use all available memory and bring your system to a halt.
A computer virus attaches itself to a program or file which enables it to spread from one computer to another, leaving infections as it travels. Viruses have different levels of severity. Some viruses have mildly annoying effects to hardware or software while some might damage your files beyond repair. A computer virus can steal your passwords, display advertisements, or crash your computer. The most dangerous type is the virus that has the capability to transmit itself across networks and bypass security systems.
A computer virus needs human interaction in order for it to be able to cause harm. Almost all viruses are attached to an executable file, which means that the virus may exist on your computer but it can only infect your computer if you choose to run or open it. A virus is spread by sharing infected or infecting files or sending emails with viruses in the attachments.
Famous viruses include the Concept virus, the Chernobyl virus (CIH), and the ILOVEYOU virus.
In a nutshell: Attaches itself to an .exe file. Requires human action to spread.
2. Worm

A worm is similar to a virus by design and is generally considered to be a sub-class of a virus. However, unlike viruses, worms don’t need human interaction. They have the capability to travel from computer to computer on their own. They take advantage of files or information transport features on your system. The biggest danger that a worm poses is its capability to replicate itself on a system. For example, a worm could send a copy of itself to everyone on your address book then it would replicate and send itself out to everyone listed in each of the receiver’s address book, so on and so forth.
Worms typically tend to consume too much system memory or network bandwidth causing web servers, network servers, and individual computers to stop responding.
Examples of worms include the Blaster Worm, which is designed to tunnel into your system and allow malicious users to control your computer remotely, and the Sasser Worm, a computer worm that affects computers running vulnerable versions of Microsoft Windows XP and Windows 2000 by exploiting the system through a vulnerable port. Other famous worms include the Morris worm, the Anna Kournikova worm, and the Storm worm.
In a nutshell: Can replicate itself on a system. Does not require human action to spread.
3. Trojan Horse or Trojan

This type of malware is named after the mythological Trojan Horse. A Trojan Horse, or simply a Trojan, appears to be useful at first by disguising itself as a legitimate file or software from a legitimate source. However, it will cause damage once installed or run on the computer. Some Trojans are designed to be more annoying than harmful while some may cause serious damage by deleting your files or deleting information on your system. Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing confidential or personal information to be compromised. For example, downloading a pirated software may actually contain a Trojan.
Some of the things a Trojan can do include monitoring activity on your computer, joining your computer to a botnet, opening floodgates, and downloading other types of malware to your computer.
In a nutshell: Appears useful but damages system. Requires human interaction. Does not self-replicate.
4. Blended Threat

A blended threat is a more sophisticated attack that bundles some of the worst aspects of viruses, worms, Trojan horses, and malicious code into a single threat. Blended threats can use servers and Internet vulnerabilities to initiate, then transmit and also spread an attack. They cause harm to the infected system on network and propagate using multiple methods. They can attack from multiple points as well.
To be considered a blended threat, the attack should normally serve to transport multiple attacks in one payload. Basically, it can cause damage within several areas of your network in just a single period of time. Because of this, blended threats are considered to be the worst risk to security since most of them require no human intervention to propagate.
In a nutshell: Sophisticated. Bundles aspects of viruses, worms, and Trojan horses. Most require no human action.
5. Spyware

A spyware is a type of malware that spies on you without your knowledge. It collects a variety of different types of data. In fact, different types of malware can act as spyware. For example, there are some spyware that get included in Trojans then spy on keystrokes to steal financial data.
In a nutshell: Spies on your computer activity. Other types of malware can act as spyware.
6. Adware

Adware is a type of malware that often comes along with spyware. It is any type of software that displays advertising on computer. However, programs that display ads inside the program itself aren’t generally classified as malware. The kind of adware that’s particularly malicious is the kind that abuses its access to your system to display ads when it shouldn’t. Adwares are considered to be more socially acceptable” than other types of Malware.
An example of an adware is the Ask Toolbar that’s included with Oracle’s Java software.
In a nutshell: Display ads. Not always a threat to your machine.
7. Keylogger

A keylogger runs in the background, recording every keystroke you make. Keystrokes can include usernames, passwords, credit card numbers, and other sensitive data. Keyloggers upload these keystrokes to a malicious server where it can be analyzed and people can pick out useful passwords and credit card numbers. Different types of malware can act as keyloggers. Employers can also install keyloggers into their employees’ computers for monitoring purposes.
In a nutshell: Records key strokes. Can be used for monitoring purposes.
8. Botnet or Bot

A botnet, also sometimes called a zombie army, is a software program created to automatically perform specific operations. Although some bots are created for relatively harmless purposes such as video gaming, it is becoming alarmingly common to see bots being used maliciously. Each of the computers functions as a “bot” because it becomes infected with a specific piece of malware. Once a botnet infects your computer, it will connect to some sort of control server and wait for instructions from the botnet’s creator. Botnets can be used to initiate a distributed denial of server (DDoS) attack.
Websites can guard against bots with CAPTCHA tests that verify users as human. According to many reports, botnets currently pose the biggest threat to the Internet.
In a nutshell: Turns computers into robots. Rely on unprotected computers that can be turned into zombies.
9. Rootkit

A rootkit is a type of malware designed to burrow deep into your computer, avoiding detection by security programs and users. A rootkit might hide itself completely, preventing itself from showing up in the Windows task manager. Once a rootkit has been installed, it is possible for the malicious party behind the rootkit to remotely execute files, access or steal information, modify system configurations, alter software, install concealed malware, or control the computer as part of botnet. The key thing that makes a malware a rootkit is that it’s stealthy and focused on hiding itself once it arrives.
Rootkits continually hide their presence and as a result, typical security products are not effective in detecting and removing toolkits. Rootkit detection therefore relies on manual methods such as monitoring your computer for irregular activity, signature scanning, and storage dump analysis. Users can protect themselves from rootkits by regularly patching vulnerabilities in software, applications, and operating systems, updating virus definitions, avoiding suspicious downloads, and performing static analysis scans.
In a nutshell: Good at hiding its presence. Activated each time your system boots up.
10. Ransomware

Ransomware is a fairly new type of malware. This type of malware holds your computer or files hostage and demands a ransom payment. Some ransomware simply pop up a box asking for money before you can continue using your computer. Most types of ransomware can be defeated by an antivirus software.
An example of ransomware is the CryptoLocker. The CryptoLocker encrypts your files and demands a payment before you can access them. The CryptoLocker is dangerous especially if you don’t have backups.
In a nutshell: Spreads like a worm. Holds your computer system captive in exchange for money.
Read about ways to get rid of malware, click *insert how to combat malware link here*. You can also read about the common symptoms of malware here.